Document Certification Through the Blockchain
Date published: 2016-12-05
Executive summary
The outlined solution illustrates how a Blockchain can solve the existing problem of verifying the validity of digital assets such as a picture of your birth certificate, a pdf document stating your will or a signed legal document specifying a business deal very efficiently and at a very low implementation cost. This example also shows that the solution relies on a number of non-Blockchain-related technologies and the Blockchain is used only for a very specific task of storing digital signatures of assets that prove their validity.
Due to the characteristics of the Blockchain (permanent decentralised ledger of information), these digital signatures can be accessed by anyone. Hence anyone with access to the Blockchain can now verify the authenticity of a digital asset without having to rely on trusted intermediaries.
The Blockchain is not the solution to the Signed Digital Asset problem. Rather it plays a small but important part in this proposed solution.
Current status quo and the problem
I’ve completed a master’s degree at Victoria University of Wellington but I’m not able (and I’m not the only one) to prove this to anybody else other than by providing the original piece of paper to support my claim.
Many business processes in government institutions and organisations alike require original documents to be provided for verification purposes before any further processing can occur. Since some documents (e.g. birth certificates) may exist only once, the parties involved may experience reluctance in handling these important documents as they could get damaged, lost in the mail, etc.
The friction is a result of
Requiring original documents to be presented to comply with the institution’s vetting and verification processes
and
The reluctance by the parties involved of having the responsibility to protect these important physical pieces of paper throughout the process.
The question is how can we create a digital proof that a digital asset (soft copy of birth certificate, your University diploma, business contract or legal document) has been certified (signed) by an authorised organisation or government institution and secondly, how can anybody around the world verify the authenticity of a particular digital asset without having to rely on a 3rd party or intermediary?
A potential solution
The solution proposed does not suggest to store the digital asset on the Blockchain (this would be a very inefficient and expensive approach). Instead it only stores the proof that a digital asset has been certified (or signed) by an institution on the Blockchain. If anybody would want to verify the legitimacy of a digital asset they can simply verify the digital asset by vetting it using the proof provided. Hence, the Blockchain’s role in this solution is to provide an immutable storage container for these proofs.
At a high level the proposed solution includes the following steps:
Creation of a digital asset and storage of the digital proof (signature) to the Blockchain
Transmission of the digital asset (Email, file sharing, etc.)
Validation of the digital asset using the signature stored on the Blockchain and vetting of the institution that issued the asset.
A more detailed discussion of these steps is outlined next.
Step 1: Digital Fingerprint
Just like the fingerprint that is unique to a human being, digital assets also have a unique 'fingerprint'. To be more exact, a digital asset's fingerprint can be created by using so called cryptographic hash functions. These functions can take a file of almost any size (word, excel, pdf, image, etc.) as an input parameter to create a string of letters and characters (its very unique fingerprint) as an output.
However, this is a one-way process as it is not possible to reproduce the file from the digital fingerprint. There are a number of different hashing functions available but for this example we use the MD5 hash algorithm.
To try this yourself, use this online MD5 hashing tool to create digital fingerprints for any file of your liking. However, if you specify this file, for example, you will (hopefully) get a 32 character long digital fingerprint of '173013304aeec4e49cc6718cb4caeccb'.
Step 2: Create a signature (JWT - JSON WEB TOKEN)
In the same way we can engage in a commercial contract by putting our 'unique' hand-written signature on a piece of paper, in Step 2, the digital fingerprint from Step 1 gets signed. In order to achieve this, Public-Private-Key-Pairs (RSA Keys) are required as an input parameter for signing the digital fingerprint.
One commonly used method to create digital signatures are JSON Web Tokens (or JWT for short). JSON Web Tokens, an open industry standard commercial tool for generating and verifying tokens, are widely available and the process is very straight forward.
-----BEGIN RSA PRIVATE KEY-----MIICXAIBAAKBgHvwpL961kgAQfzx3vcVkFou3wPcpFytrM1GXVXbYp+P9ASM285nvN1AQZ2YfpzII1jnYvy67WtGDUJPOKRejwcArY/w7vuhiiWGZ58OhV9MZLWI7xJ7LYVSTGOm58AYe6w0H2xNeP3WPfB31sfq2Jd4d/wJE0876jbbfr424lZXAgMBAAECgYAtm9e0kwqJwnaGE6feOzQ8y6TL8gUWCd9eRveP4cTAPSQqDH/SzAAHV18OFJD7Nvcy/ytBH7TA1i2I6khIzHdLM4Gzb4tSv++pvx6rZX12HMxyRqBrK/HGXfro0c2xpvt/DYtjajB4J0vIDFzxBL+QK7fahWcGHbbQsRvowGIoYQJBAMbpi8kyUaksxOvNUFeXpBgw4d2k2dabnBxH5fmKJnx9E7sY2VQbLlXXeFVBJkeXUR6xDhw3fFBbnWeW1YKCYKcCQQCfgr7moKtWNPWIlbdi91TUtGeQ5NRm/k6mV3hJslr2qmMXA3FyL8qOuHHUC3ljpOr8L2CuLrMe4YIcgcNbsuLRAkEAisJlR2eY2+FlRfGmOFSKnm2LQuk7JaDMGFZ3scqT6of+eahuA2QqwKtdQGwAXjTK3BQ7eaejSxN+DMOGElMNRQJAWcZHVRv2cpVp346L4Spc1z4Vz+nKVZEpiNtP+wJjydJJ5MjuT5rwQPU0M2il0FwgWQD9Q+tKqsW26f5qijCbEQJBALR3J33gDLGDiX0VAi2ea0Dcq1H+NRl26Mr0Yb+ls0qQQwizNoda3jx4MEkk0UDQlmtb5jRvyKvScsr91gxXbx8=-----END RSA PRIVATE KEY-----
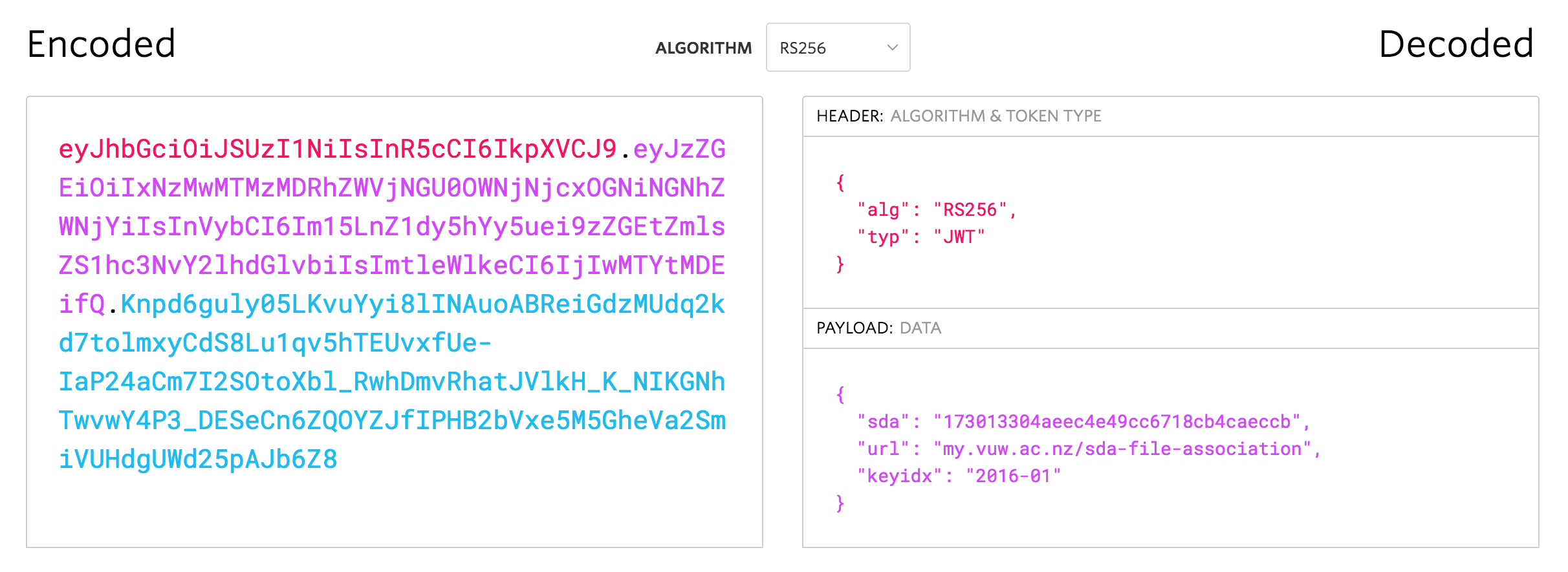
{
"sda": "173013304aeec4e49cc6718cb4caeccb",
"url": "my.vuw.ac.nz/sda-file-association",
"keyidx": "2016-01"
}To create a JWT yourself, a very useful online tool is called jwt.io. An example of a valid JWT for the digital fingerprint ('173013304aeec4e49cc6718cb4caeccb') created in Step 1 using the RSA private key ("----- BEGIN RSA PRIVATE ...") may look like the image below. The sda field in the payload holds the digital fingerprint. The relevance of url and keyidx will be discussed later. If you use jwt.io do not forget to change the Algorithm in the drop down to 'RS256'.
Note: Only parts of the RSA private key, sda and url are shown here, scroll horizontally to copy all the information. Important: As this is only an example outlining a solution, the private key is shared. As the name suggests, in practice this private key should never be shared and should be protected ( kept private) at all costs. Do not use this private key for anything else other than in this example solution!
STEP 3: COMMIT FINGERPRINT AND Signature TO BLOCKCHAIN
In the last step, the digital fingerprint and the JSON Web Token (Signature) are 'uploaded' to the Blockchain. This is now the first time in this solution an interaction with a Blockchain is required. It is important to keep in mind that not the digital asset itself but only the information about the asset (its fingerprint) and the signature get stored on the blockchain. In the technical section of this solution (see below) the source code can be downloaded for further information.
Step 4: Transmission of the signed digital asset
Using our existing ways of sharing information with tools such as email, online forms, file sharing platforms, etc., the digital asset can now be distributed to any party since it is a file like any other one. Note: There is no need to share the digital asset's fingerprint and the signature as they are stored on the Blockchain. Only the digital asset itself should be shared.
Caution: Any modification to the digital asset would also cause its digital fingerprint to change. As a result, the signature (JWT) stored on the Blockchain would no longer match the digital asset’s new fingerprint. Hence the new digital asset can no longer be considered as 'valid' as no corresponding signature exists.
To test this yourself, choose an image and create its digital fingerprint as we’ve done in Step 1. Open an image editor such as paint and change only one pixel, save the file and re-create its digital fingerprint. As you’ll see, the digital fingerprints do not not match.
STEP 5: DIGITAL ASSET VERIFICATION
The process for the recipient to verify the authenticity of a digital asset is similar to the steps performed earlier starting with re-creating the digital fingerprint from the file that has been received. Next a request is launched to the Blockchain to retrieve the fingerprint’s corresponding signature (JWT). Lastly, 'apply' the RSA public key that corresponds to the RSA private key that has been used in Step 2 to verify the signature and consequently the validity of the digital asset.
-----BEGIN PUBLIC KEY-----MIGeMA0GCSqGSIb3DQEBAQUAA4GMADCBiAKBgHvwpL961kgAQfzx3vcVkFou3wPcpFytrM1GXVXbYp+P9ASM285nvN1AQZ2YfpzII1jnYvy67WtGDUJPOKRejwcArY/w7vuhiiWGZ58OhV9MZLWI7xJ7LYVSTGOm58AYe6w0H2xNeP3WPfB31sfq2Jd4d/wJE0876jbbfr424lZXAgMBAAE=-----END PUBLIC KEY-----
Let's say you received this file via email and you want to verify its validity. To do this, start by re-creating its digital fingerprint with the online MD5 hashing tool as we've done in Step 1 to get '173013304aeec4e49cc6718cb4caeccb'. Next, go to this site, paste the fingerprint into the text field and push the 'Query' button to get JWT returned.
Congratulations, you've just queried data from a Blockchain!
Use jwt.io and paste the JWT into the text box and ensure the fingerprint matches the fingerprint specified in the sda field (click the image on the right to enlarge it for comparison). However, as you can see, the Signature is still invalid. As the final step, copy the RSA public key ('-----BEGIN PUBLIC KEY----- ...') into the 'Public Key or Certificate' field to get a Signature Verified confirmation.
STEP 6: CERTIFICATE PROVIDER IDENTITY VERIFICATION
The last step of the verification process is to verify if the institution that created this digital asset is a legitimate entity itself. Since anybody can create, sign and commit information to the Blockchain and pretend to be somebody else this is a very important step in the verification process.
Fortunately, this challenge has already been solved as well and it is called Extended Validation SSL where the certificate authority (the entity issuing SSL certificates) is required to conduct a thorough vetting of the institution by:
Verifying the legal, physical and operational existence of the entity and
Verifying that the identity of the entity matches official records among further checks.
By using the URL that has been specified in the JWT we can now verify if and what SSL certificate has been provided by the institution behind this URL. This allows us to trust (or not) the legitimacy of the institution that created the signed digital asset in the first place.
Some examples of New Zealand institutions using Extended Validation SSL certificates are: NZ Government Department of Internal Affairs, ANZ, ASB, BNZ, Kiwi Wealth. By loading these institutions' websites your browser will indicate the existence of an Extended Validation SSL certificate as shown in the image on the right.
The technical implementation details
In this example the Blockchain Ethereum is used.
EXTENDED validation SSL
An institution that wants to sign digital assets should go through the required process to obtain an extended validation SSL certificate. As mentioned earlier, this certificate provides the highest level of trust in the legitimacy of the institution.
RSA PUBLIc-private KEY PAIR
Generating RSA public-private key pair is a common process that can be achieved through various tools. For testing purposes only you can create a key pair using this site. Next only the public keys need to be made available to the public by publishing these on the institutions website (that has been secured with the extended validation SSL certificate).
For example, Victoria University of Wellington might publish this file at the URL my.vuw.ac.nz/sda-file-association. Using martinstellnberger.co as another example of someone who wants to sign digital assets, the public key file hosted on this website could look like this (www.martinstellnberger.co/assets/keys/sda-file-association.json).
CREATE AND DEPLOY CONTRACT ON ETHEREUM BLOCKCHAIN
Using this code, an institution can deploy its own contract on the Blockchain. This contract now serves the role of an immutable storage container for all the institution’s digital asset signatures.
When this code gets deployed on the Ethereum Blockchain a contract gets created at its unique 42-character long address (e.g. 0xd2982ef0ce43092248efe738104ff5691e0d89f0). Click on this address to view more details on this contract on the Blockchain on etherscan.io website. This address is important and will be used next.
CREATE DIGITAL ASSET, FINGERPRINT, JWT AND UPLOAD TO BLOCKCHAIN
Now, the institution creates a digital asset that also contains the visual information of the Blockchain contract’s address (e.g. QR-Code as shown at the bottom right of this document). Next, the digital fingerprint and the JWT are created. Using the contract’s add function the JWT and its signature are added to the contract for storage.
Further areas of improvement
This proposed solution illustrates how Blockchain technologies could be utilised to solve the problem of verifying digital assets. This solution purposefully did not include some useful additional features and optimisations such as:
Time stamping of signatures so that they can expire.
Since storage is very expensive on the Blockchain, the goal is to store as minimal information as possible on the Blockchain. Hence, the URL and Keyidx could be stored with Blockchain contract and not be part of the JWT.
To optimise storage further, the JSON web token could be replaced with only the signed digital fingerprint. It is even possible to store the JWT off the Blockchain entirely.
Use interface base contract that establishes a standard for signed digital asset verification.